Remote Working: How Can We Keep Our Organisations Safe?
Three years ago, most people wouldn’t have dreamt that they would be able to spend most, if not all, of their working hours outside the office environment. However, despite coronavirus restrictions on where we can work being a thing of the past, remote working is here to stay.
Even though we’re living in the ‘new normal’, it seems that many organisations’ approach to cybersecurity hasn’t quite caught up. In fact, our research reveals almost half (48%) of IT decision makers admitted that their organisation’s cybersecurity has been proven not to be good enough for remote working, whilst more than one in three (37%) admitted that employees in their organisation haven’t been educated on how to avoid a security breach.
Remote, flexible and hybrid working has become increasingly commonplace across almost every sector, creating a need for cybersecurity solutions to adapt and evolve. Our research* highlights the biggest risks organisations are facing, how these are impacted by remote working and how we should adapt cybersecurity strategies to ensure operations continue without interruption.

Where do IT leaders think their biggest risks lie?
- Due to advancements in threats and technology, the technical debt in their cybersecurity strategy will leave their organisation increasingly exposed (46%)
- Business line IT – employees/end users downloading line of business applications that haven’t been IT assessed and could be a gateway for hackers (43%)
- The lack of full status visibility across their cybersecurity solutions (37%)
- Employees not being educated enough on cybersecurity threats (36%)
- An increasingly remote workforce, where employees are working from multiple places and devices (36%)
- The fact that hackers are becoming more sophisticated (35 %)
Each of the risks identified by IT leaders are exacerbated when employees are working remotely, across multiple devices, platforms and locations. As a result, it is of the utmost importance that organisations ask themselves: how can we mitigate these risks whilst maintaining the ability to work flexibly?
“As dynamic work becomes the new reality, the future of work will depend on employee and consumer experience. People now come to expect the freedom to work on their own terms.
“Organisations that harness a strategic approach to work and identity will be able to optimise this experience, drive productivity and enable their employees to flourish in the new world of work.” Pete Wilson, Director, EMEA Partnerships, Okta
Plugging the gaps
Since the introduction of homeworking, organisations have had to diversify significantly and react to limitations which were implemented with little to no warning. This has ultimately led to IT leaders identifying gaps in their cybersecurity strategy.
With over 2 in 5 identifying technical debt in their cybersecurity strategy as the biggest risk to their organisation’s cybersecurity, a simple start is to cross-check and align your security strategy against the NIST cybersecurity framework.
The framework, published by the US National Institute of Standards and Technology, consists of standards, guidelines, and best practices designed to help organisations assess the risks that they face and to improve their management of cybersecurity risk overall.
Performing the framework’s five key functions of identification, protection, detection, response and recovery, concurrently and continuously ensures you have the right tools in place. Your organisation will not only be able to see threats, but also react accordingly in a timely manner.
The NIST cybersecurity framework is designed to integrate with existing security processes within any organisation and in any industry, whether completely office based or remote.
Multi-cloud security
Cloud usage is becoming increasingly commonplace and is now usually the preferred option when organisations procure new IT services. As a result, cloud security has become a necessity for many. Cloud security is a collection of cybersecurity measures and procedures designed to protect cloud-based infrastructure, applications, and data. These measures ensure data and resource access control, data privacy protection and support regulatory data compliance.
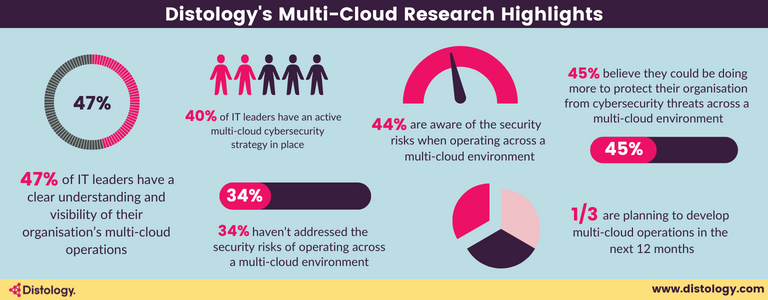
As flexible working is the new globally accepted norm, many organisations are beginning to operate across multiple clouds. Our research shows that average company is using 2.2 public clouds, while 87% are operating across a hybrid or multi-cloud deployment and so the need for a modern multi-cloud security strategy has never been greater. The modern day consumer wants the ultimate user experience, which gives them access to what they need, when they need it, without facing any sort of friction on their way to consuming their online product or service. They also need reassurance that their data is both safe and secure.
Most of us are experiencing working across multi-cloud platforms for the first time, so it’s no surprise that many IT leaders are unsure which security measures are needed to protect their organisation, its people and customers.
Our research shows that two in five (42%) IT leaders are planning to invest in multi-cloud operations, but migration, skills and security are some of the top fears about integration.
This is where the multi-cloud solutions currently on the market come in to play. From network security and cyber asset visibility, to API protection and ensuring data is kept safe and secure, multi-cloud security solutions such as Okta, Auth0, ThreatX, Cyolo, Fortanix, Harbor Solutions and Wiz, help protect from external threats and prevent deep impact when they do happen. They also ensure that both the network and cloud-based applications are understood and secured. These solutions help to ensure the user experience is not compromised as a result of a robust cybersecurity process running in the background.
“IT leaders face a challenging combination of data sprawl across public and private clouds, data warehouses, data lakes etc., and the proliferating data privacy regulations around the world. They have had a hard time just knowing where data is, let alone managing it effectively.
“While legacy encryption technologies created for the on-premises era may have severe limitations, they would do well to consider emerging technologies that have been developed for the multi-cloud era, with centralised controls via single dashboards, capabilities like bring your own key (BYOK) and confidential computing, and a zero trust approach to protect critical data in a multi-cloud environment.” Gerry Sillars, Vice President International, Fortanix
The power of people
So you’ve put all the right solutions in place, surely you can relax now? Unfortunately, not quite.
Even with all the best solutions in place, people will always continue to be the weakest point in the chain of defence. Training employees to understand the cybersecurity risks and spot potential security breaches/attacks should still be prioritised.
From connecting to an unsecure network to phishing emails, and using the same password across multiple devices/platforms, there are a number of ways employees can fall victim to a security breach, that could have a detrimental (not to mention costly) impact on the organisation.
Over half of those we surveyed (55%) told us that they planned to implement a cybersecurity training and testing programme for all employees within the next two years.
Working for home has undoubtedly changed the cybersecurity landscape, making it easier for threat actors, cyber criminals and hacktivists to gain entry to employees’ network and/or accounts, so we must ensure that all employees are equipped with the knowledge to spot and prevent this activity, where possible.
Whilst there will never be a one size fits all approach to cybersecurity, there are a variety of solutions and approaches to suit all types or organisations and ensure they are both protected and operating with minimum risk and maximum visibility.
To find out more about the cybersecurity solutions available to help protect organisations against the threats associated with remote and flexible working, get in touch with our team of experts.
*Based on a survey conducted in October 2021 of 250 IT decision makers, including IT managers, IT directors, CIOs, COOs/operations directors who are responsible for purchasing IT



