Make Your Life Easier with Axon
LogRhythm Axon is a cloud-native SaaS SIEM platform built for security teams that are stretched thin by overwhelming amounts of data and an ever-evolving threat landscape. Optimised for the analyst experience, Axon’s intuitive workflow gives analysts contextual analytics into cybersecurity threats so you can reduce noise and quickly secure your environment. Axon reduces the burden of managing threats and the operating infrastructure, helping security teams prioritise and focus on the work that matters.
Ready for an inside look?
Learn how you can improve your enterprise’s hybrid IT security posture.
How LogRhythm Can Help
LogRhythm gives you a complete and accurate model of end-to-end activity at the network, host, and user level. It delivers an intelligent approach that can automatically monitor for threats, recognise suspicious behaviour, and develop a baseline of normal network activity.
Ease your analyst experience with:
A comprehensive
ML-driven solution
![]()
A built-in MITRE ATT&CK™ engine
![]()
20,000+ out-of-the-box detection rules
![]()
Weekly updates and ML-based tuning
![]()
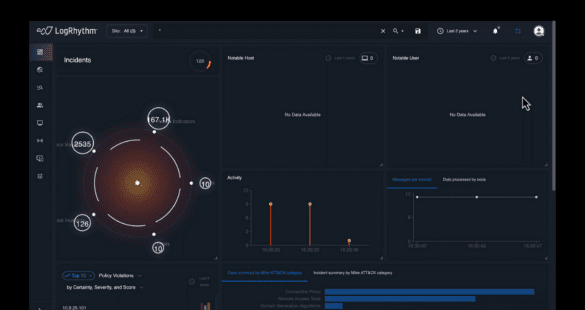
LogRhythm NDR User Interface Walkthrough
LogRhythm Network Detection and Response (NDR) enables overwhelmed security teams to detect network cyberattacks efficiently and effectively with advanced analytics.
NDR collects user and host data across the network and analyses both deterministic and undeterministic rules with machine learning to gain seamless visibility, reducing the dwell time of threats outside the perimeter.
With LogRhythm NDR, security teams can easily hunt and investigate surfaced incidents to help reduce the cost associated with attacks that usually go unnoticed.
Defend Against Cyberattacks with LogRhythm SIEM
Gain visibility, protection and threat detection across all surface areas, systems and assets with LogRhythm SIEM.
Watch this video to find out how LogRhythm accurately pinpoints cyberthreats and empowers professionals to respond with speed and efficiency.
LogRhythm Integrations
Customer Case Studies

Coleg Cambria
Education
“The benefits of this platform also go beyond threat detection. The platform has identified potentially dangerous holes in our existing security tools and processes. Furthermore, we realised that when staff left the college, their accounts weren’t being deactivated in a consistent manner in line with our operating procedures. By highlighting this, LogRhythm has helped us improve our security programme significantly.” Robert Green, Security Analyst.

McColl’s Retail Group
Retail - Convenience
“We were able to create a commercial strategy that worked for every McColl’s store. We were not the regular customer for security firms at the time, but LogRhythm worked with us instead of forcing us into a solution that would not be of use.” Peter Gore, Development & Compliance Manager.

Salford Royal NHS Trust
Healthcare
“We did try a different vendor before the LogRhythm installation, but it was not at the level of quality that we needed. We required a solution that was more precise and thorough. A number of our partners used LogRhythm and highly recommended the solution to us, so we had that in the back of our minds when it came to finding a solution that was a better fit for us,” Donald Andango, Information Security Specialist.
Request a Demo
Ready when you are! Take a quick demo with one of our experts and learn why millions of people rely on LogRhythm to give them the ability to detect, react to and report threats on their networks.